Microsoft has set a firm timetable to make all of its products and services quantum safe. The company plans to enable early adoption starting in 2029 and complete the transition by 2033. That schedule arrives two years ahead of many government completion targets, and it signals how urgent the shift to post quantum cryptography has become for the wider ecosystem.
This move matters because the world’s digital backbone still relies on public key cryptography that future quantum machines could break. Attackers already harvest encrypted data today, with plans to decrypt it later. Therefore, organizations cannot wait for quantum hardware to arrive at scale. They need a roadmap, budget, and engineering plan for quantum safe upgrades now.
Microsoft is folding the timeline into its Quantum Safe Program, an initiative that coordinates standards work, engineering changes, and customer guidance across Windows, Azure, Microsoft 365, and more. The company has begun shipping post quantum cryptography support in its SymCrypt library and has even released early PQC capabilities to select Windows and Linux users so enterprises can test compatibility.
The plan lands as policy momentum accelerates. The U.S. National Institute of Standards and Technology finalized the first NIST PQC standards in August 2024. At the same time, U.S. National Security Systems are working toward the CNSA 2.0 transition, which sets staged milestones and expects full adoption across key classes of technology by the early 2030s. As a result, Microsoft’s 2033 date aligns with the most demanding government tracks and gives customers a clear north star.
What is changing and when
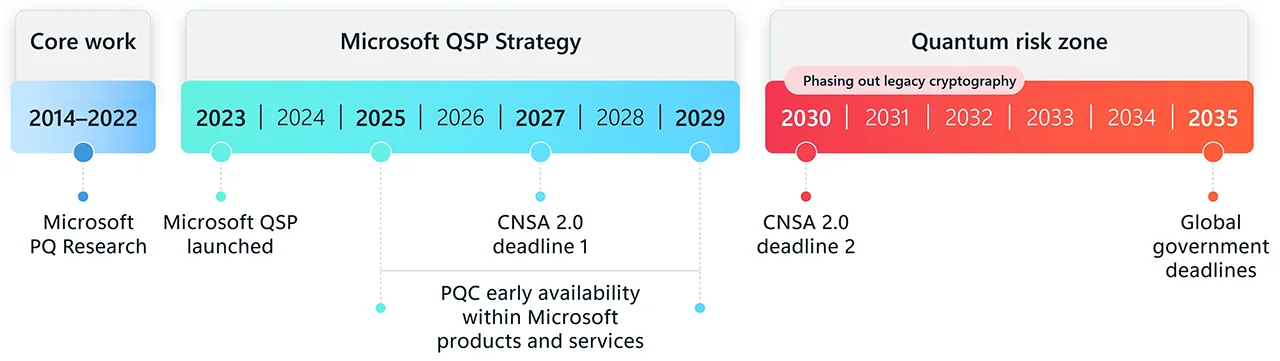
Microsoft’s quantum safe timeline has two clear waypoints. The company aims to make PQC features available for early adopters by 2029. It then plans to turn those capabilities on by default and complete the companywide transition by 2033. Microsoft presents this as a deliberate, multiyear journey rather than a flip of a switch.
The roadmap follows active standards work. NIST’s finalized suite includes ML KEM for key establishment and ML DSA and SLH DSA for digital signatures. Those algorithms are now formal FIPS standards and ready for implementation across products and protocols.
Meanwhile, CNSA 2.0 provides concrete milestones for National Security Systems. For example, browsers, servers, and cloud services should prefer CNSA 2.0 algorithms by 2025 and use them exclusively by 2033. Operating systems should reach exclusive use by 2033 as well. These dates set strong signals for vendors and large enterprises planning their own rollouts.
How Microsoft plans to get there
Microsoft outlines a phased engineering program that flows from cryptographic plumbing to platform defaults. First, the company is adding PQC algorithms into SymCrypt, the core crypto library that underpins Windows, Azure, Microsoft 365, and other platforms. Next, it will update foundational services such as Entra authentication, key and secret management, and signing systems. Finally, it will integrate PQC across Azure services, Microsoft 365, data platforms, AI services, and networking so quantum safe protection becomes ubiquitous.
The SymCrypt work is already visible. Microsoft has begun releasing support for ML KEM and XMSS, with ML DSA and SLH DSA following. The company is also contributing to IETF efforts to standardize quantum safe key exchange and authentication for TLS, SSH, and IPsec. Early enablement for Windows and Linux gives customers time to test dependencies and uncover issues like header size or certificate chain impacts before defaults change.
Why this urgency now
Experts differ on when a cryptanalytically relevant quantum computer will arrive. However, the policy and standards communities have chosen to act early. NIST’s standards remove a key blocker, and CNSA 2.0 sets a managed glide path that culminates around the early to mid 2030s. Microsoft’s 2033 target places the company ahead of that curve and offers customers a practical anchor date for their own roadmaps.
There is also a strategic wrinkle. Microsoft is investing to make quantum computing practical, including a February 2025 reveal of Majorana 1, a topological quantum processing unit designed to scale to a million qubits on one chip. That research does not diminish the PQC push. Instead, it reinforces why the global ecosystem must become quantum safe before large scale quantum computers emerge.
What security teams should do now
Inventory and classify crypto. Start with a full inventory of cryptographic assets, protocols, certificates, hardware modules, and embedded dependencies. Tag systems that face the public internet or hold sensitive data. This baseline will determine scope and priority, and it aligns with Microsoft’s advice to customers that the transition is a multiyear program requiring coordinated execution.
Adopt crypto agility. Design for algorithm agility so you can rotate from classical to hybrid to pure PQC without major rewrites. That includes using modern APIs, avoiding hard coded algorithm choices, and preparing for larger keys, signatures, and certificate chains as PQC becomes standard.
Pilot PQC early. Use preview builds and test environments to trial ML KEM, ML DSA, and SLH DSA in TLS, code signing, device trust, and identity flows. Validate performance, packet sizes, and interoperability. Address impacts on middleboxes, legacy agents, and firmware update paths.
Map to policy timelines. Align your milestones to CNSA 2.0 and sector guidance. For mixed environments, plan hybrid deployments that pair classical and PQC algorithms to maintain compatibility during the transition window.
Educate stakeholders. Ensure product owners and legal teams understand “harvest now, decrypt later,” data retention risks, and vendor dependencies. Budget for certificate lifecycle changes, HSM upgrades, and protocol migrations over several fiscal cycles.
The bigger picture
The quantum safe transition is not just a Microsoft project. It is the next chapter in internet security. Standards are here. Government timelines are firming up. Vendors are baking PQC into libraries and stacks. The work will take years, yet starting now reduces operational risk later. Microsoft’s 2033 commitment offers a clear signal that the industry is moving from theory to implementation. The organizations that treat this as an engineering program, not a checkbox, will be best placed when the quantum era goes from possible to present.
Keywords to reinforce relevance: quantum safe, post quantum cryptography, PQC, NIST PQC standards, CNSA 2.0, Microsoft Quantum Safe Program, SymCrypt, ML KEM, ML DSA, SLH DSA, Windows, Azure, Microsoft 365.

